This post shows two examples which shows how to verify signature of an application based on Authenticode policy. First example will fail, because the application is signed with the key, whose root certificate is not trusted.
Example 1 (it will fail)
C:\Program Files\Microsoft SDKs\Windows\v6.0A\bin>signtool verify /v /pa c:\temp
\SampleApplication.exe
Verifying: c:\temp\SampleApplication.exe
SHA1 hash of file: 99CE8EA6C1096C7CF9CD96C4A2E707A096CA1E76
SignTool Error: WinVerifyTrust returned error: 0x800B010D
The certification path terminates with the test root which is not truste
d with the current policy settings.
Signing Certificate Chain:
Issued to: Root Agency
Issued by: Root Agency
Expires: 01.01.2040 01:59:59
SHA1 hash: FEE449EE0E3965A5246F000E87FDE2A065FD89D4
Issued to: daenetauthenticode
Issued by: Root Agency
Expires: 01.01.2040 01:59:59
SHA1 hash: 79FBF8FAE05640808B8B488BD5728B59B19D0766
File is not timestamped.
SignTool Error: File not valid: c:\temp\SampleApplication.exe
Number of files successfully Verified: 0
Number of warnings: 0
Number of errors: 1
Example 2 (it will succeed)
Now after the root certificate is installed under trusted publishers, the same verification will pass successfully.
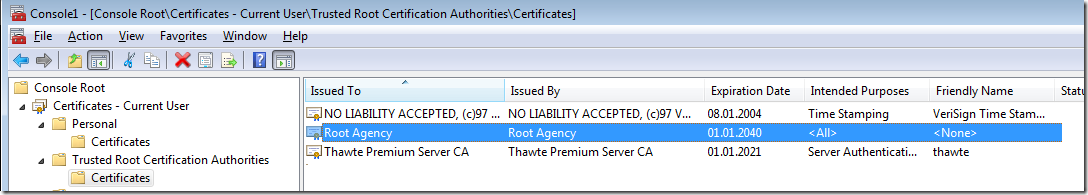
C:\Program Files\Microsoft SDKs\Windows\v6.0A\bin>signtool verify /v /pa c:\temp
\SampleApplication.exe
Verifying: c:\temp\SampleApplication.exe
SHA1 hash of file: 99CE8EA6C1096C7CF9CD96C4A2E707A096CA1E76
Signing Certificate Chain:
Issued to: Root Agency
Issued by: Root Agency
Expires: 01.01.2040 01:59:59
SHA1 hash: FEE449EE0E3965A5246F000E87FDE2A065FD89D4
Issued to: daenetauthenticode
Issued by: Root Agency
Expires: 01.01.2040 01:59:59
SHA1 hash: 79FBF8FAE05640808B8B488BD5728B59B19D0766
File is not timestamped.
Successfully verified: c:\temp\SampleApplication.exe
Number of files successfully Verified: 1
Number of warnings: 0
Number of errors: 0
Posted
May 02 2009, 04:37 PM
by
Damir Dobric