Visual Studio 2012 offers a new version of Service Bus Explorer which is fully integrated with Visual Studio. This version is installed with Windows Azure Authoring Tools Oct 2012, which is version 1.8.
To show up the explorer open the Server Explorer (View | Server Explorer) , go to Windows Azure Service Bus, right mouse click “Add new Connection”. Add connection wizard will appear (s.ee picture below).
This wizard can be used to setup connection to both Windows Azure Service Bus and to Service Bus Server.
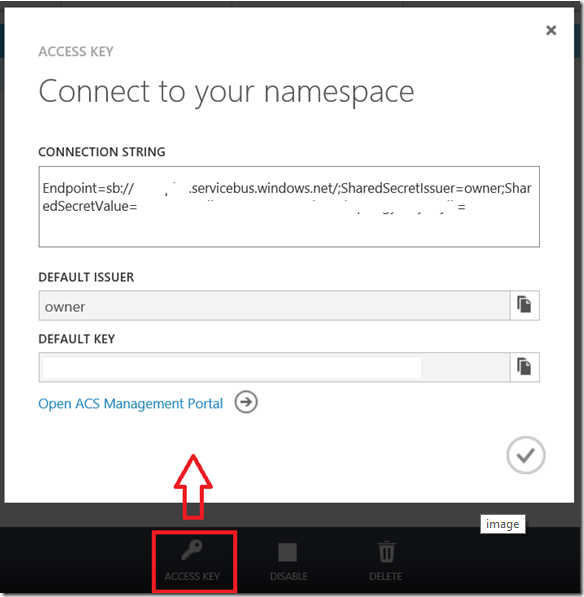
Setting up connection properties of Windows Azure is straight on. You have to just apply namespace, owner and the key. All tree can be obtained in Windows azure management portal.
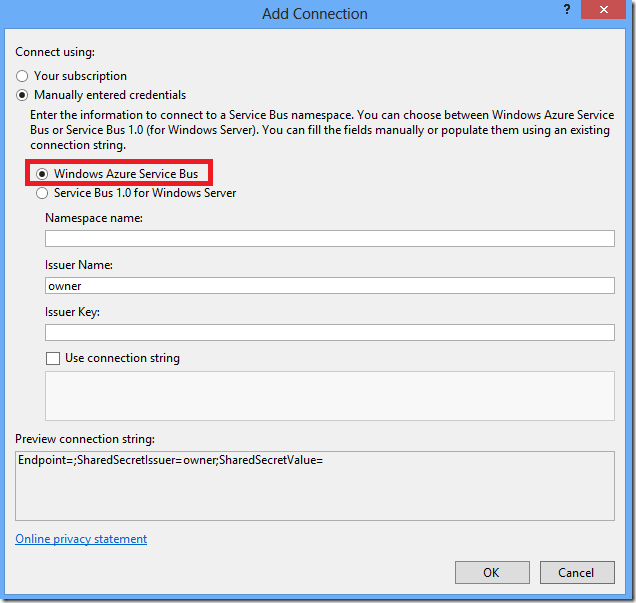
Connecting to Server version of service Bus is a bit more complicated. In this case you have to enter Service Bus endpoint which is by default listening on runtime port 9354. The STS endpoint of Service Bus for Server looks in reality like following URL example:
https://servicebus.daenetlabs.com:9355/WorkflowDefaultNamespace/$STS/Windows/
This is exactly what you should not use as URL! The URL of the STS should be exactly the same one like Service Bus endpoint with exception in port number:
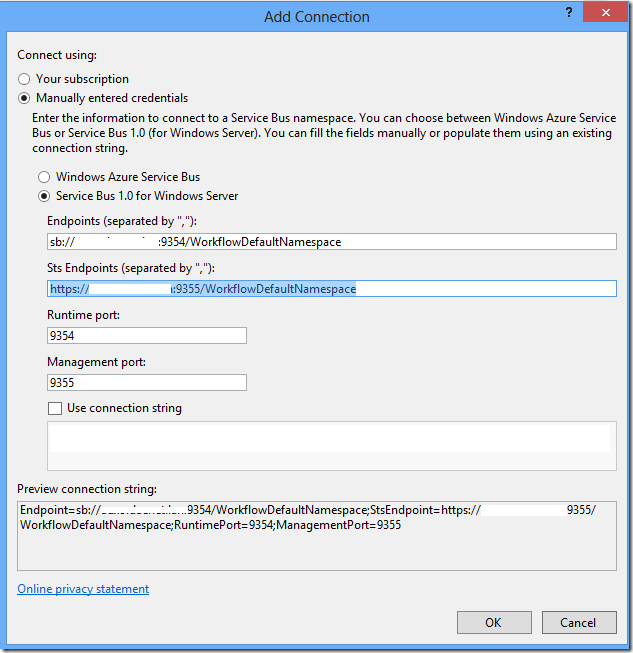
If you are running Explorer on the Service Bus box, this will work and you can connect. But if you are connecting to service bus form some other machine (usual case at least in production) this will NOT work.
The reason for this is that you have to setup the certificate trust chain before you connect. To fulfill this requirement you have to install the trust for Service Bus certificate (AppServerGeneratedSBCA) only. If you have also installed Workflow Manager
there is an additional certificate for Workflow Manager (AppServerGeneratedWFCA). You don’t have to install trust for this one, but it is probably good practice, because you will need the trust to be able to manage Workflows.
Open certificate management tools in MMC for local machine at the machine which hosts Service Bus (and Workflow Manager in my case). Then export both certificates (no need to export private key).
NOTE that this will help to mage management point working well, but runtime endpoint will not work, because certificate chain trust. This post describes how to do that.
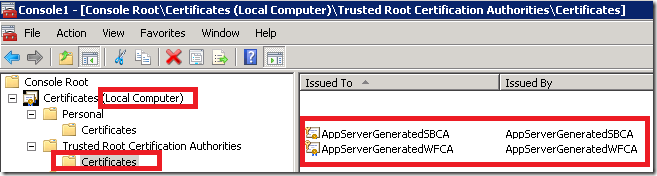
At the end, import both certificates to your machine (machine used to connect to SB from wizard shown above). Import both certificates in Trusted Authorities hive.
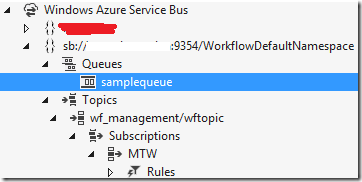
Now, you can connect.
After you have successfully connected you will notice that all SB-connections to WAZ and to Server appear in the list of connections:
Posted
Jan 03 2013, 06:20 PM
by
Damir Dobric